IoT is a booming industry and a very vulnerable domain in technology in this decade. It has been seen that various companies and their products are designed to effectively connect to a network and establish communication. These connections are through a set of protocols which are security-less protocols.
In this, we will discuss about several hacks that are possible in this domain with the use of some hardware devices as well. First let us find the way in which we can effectively test these.
Attack Surfaces In IoT Devices –
- Firmware
- Hardware
- Software
- Radio
- Cloud
Attack Methods in IoT Devices –
- Firmware
- Firmware Reversing – Reverse Engineering the firmware of IoT devices
- Scripting in Firmware – Adding malicious scripts into firmware
- FileSystem Access – Accessing the files in firmware through reverse engineering
- Hard Coded Password Grabbing – Reverse Engineering firmware binaries to extract hardcoded passwords present in IoT device
- BlueBorne Attacks
- BlueSmack – DoS for Bluetooth enabled devices
- BlueSnarf – Theft of Information from bluetooth enabled devices
- BlueJacking – Sending Unsolicited Messages through OBEX protocol in bluetooth enabled devices.
- Wireless Attacks – Wi-Fi
- Wifi Packet Sniffing – Sniffing of packets which are being sent between IoT devices through Wi-Fi
- Wifi DoS Attack
- ZigBee Framework
- Zigbee Sniffing – Sniffing the packets being sent between IoT devices through Zigbee Protocol
- Packet Replay Attack – Recording approved traffic on a network and replaying it to perform the same set of actions when necessary
- Radio Frequency Attacks
- Radio Communication Replay Attack – Recording radio frequencies and replaying them to perform the same set of actions when necessary
- Crypt Analysis Attack – It is reversing the communication flow of the IoT device, where the original data which is transmitted to IoT device is analysed and then reversed for obtaining the binary form
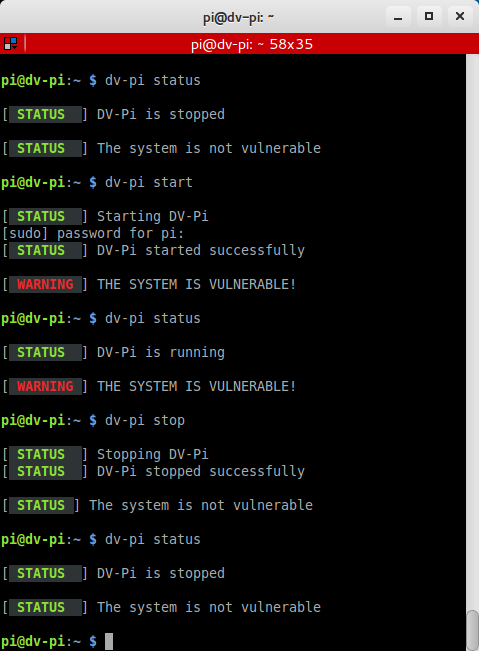
Let us now take a raspberry pi on the network and configure it to be vulnerable. I am using a vulnerable OS for this.
DV-Pi3 OS – https://whitedome.com.au/re4son/download/sticky-fingers-dv-pi-3/
Balena Etcher – https://www.balena.io/etcher/
Download the files and images of DV-Pi and the etcher software. Using etcher software install the OS onto the memory cards. Insert memory cards into pi and boot up the OS. Now the OS is vulnerable with many services in it and can be used to test legally. Connect this Pi to the network to get an IP and the test network is ready for hacking.