Beginner 1
Its base 64 string given cnRjcHt5b3VyZV92ZXJ5X3dlbGNvbWV9
Use base64 decoder and it gives rtcp{youre_very_welcome} which is flag.
Beginner 2
72 74 63 70 7b 62 6f 62 5f 79 6f 75 5f 73 75 63 6b 5f 61 74 5f 62 65 69 6e 67 5f 65 6e 63 6f 75 72 61 67 69 6e 67 7d
It is base 16 or hexadecimal string convert from hexadecimal to ascii to get the flag
rtcp{bob_you_suck_at_being_encouraging} which is the flag
Beginner 3
162 164 143 160 173 163 165 145 137 155 145 137 151 137 144 151 144 156 164 137 153 156 157 167 137 167 150 141 164 137 157 143 164 141 154 137 167 141 163 137 157 153 141 171 77 41 175 this is given which is in octal representation
Convert this octal to ascii to get the flag which is rtcp{sue_me_i_didnt_know_what_octal_was_okay?!}
Beginner 4
A text is given which is in the form of egpc{lnyy_orggre_cnegvpvcngr}
This is caesar cipher as caesar is given in the question also we can see the format of the flag reflecting in this
Caesar cipher decode with key=13 to get the flag which is rtcp{yall_better_participate}
Beginner 5
A morse code is given which is — .- -. -.– ..–.- -… . . .–. … ..–.- .- -. -.. ..–.- -… — — .–. … which is to be decrypted.
Convert morse code to text which gives many_beeps_and_boops and hence the flag is rtcp{many_beeps_and_boops}
Beginner 6
A set of number is given 26 26 26 26 26 26 26 26 19 12 5 5 16 9 14 7 9 14 16 8 25 19 9 3 19
Here we can observe numbers range from 1-26 hence we can say it is A1Z26 cipher which can be decoded also as A=1, B=2, C=3, …, Z=26.
The word we get is zzzzzzzzsleepinginphysics and the flag is rtcp{zzzzzzzzsleepinginphysics}
Beginner 7
The text is given as igxk{fmovhh_gsvb_ziv_nvzm} this can be caesar but the same concept will not given twice so we have to look for other forms of substitution cipher one of them which is hint in the question is ATBASH cipher. Using rumkin.com tools we can decrypt the atbash by pasting the above string.
We get the flag as rtcp{unless_they_are_mean}
Beginner 8
The question gives binary numbers 00110 01110 00100 00000 10011 00101 01110 01110 00011 00011 01110 01101 10011 10010 10011 00000 10001 10101 00100 . We can use these binary numbers to convert to text using Bacon cipher as given in question. Bacon cipher uses ‘a’ and ‘b’ which can be taken as a=0 and b=1 or vice versa.
Using a=0 and b=1 bacon cipher decode gives GOEATFOODDONTSTARVE and the flag is rtcp{GOEATFOODDONTSTARVE}
Beginner 9
This gave a file which had the contents in form of Base64 which can be decoded
The file contents are as follows MmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMGEgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmQgMmQgMmQgMmQgMmQgMjAgMmUgMmQgMmQgMmQgMmQ=
Decode this from base 64 to get
2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 0a 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2e 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2d 2d 2d 2d 2d 20 2e 2d 2d 2d 2d
This is hex code so decode from hex code
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– .—- .—- —–
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– .—- —– .—-
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– .—- .—- —–
—– —– .—- —– —– —– —– —–
—– —– .—- .—- .—- —– —– .—-
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– .—- —– .—-
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– .—- .—- —–
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– .—- —– .—-
—– —– .—- —– —– —– —– —–
—– —– .—- .—- —– —– .—- —–
—– —– .—- .—- —– .—- .—- —–
—– —– .—- —– —– —– —– —–
—– —– .—- .—- .—- —– —– .—-
This is morse code as output so decode from morse code we get,
00110010 00110110 00100000 00110101 00100000 00110010 00110110 00100000 00111001 00100000 00110010 00110101 00100000 00110010 00110010 00100000 00110010 00110110 00100000 00110010 00110101 00100000 00110010 00110110 00100000 00111001
After converting to text we get 26 5 26 9 25 22 26 25 26 9 which is A=1, B=2, …, Z=26 cipher which can be decoded as zeziyvzyzi
This is not final output as this can be decoded again using substitution ciphers which is abcdefghijklmnopqrstuvwxyz=mlkjihgfedcbazyxwvutsrqpon where from half of alphabets is reversed just like Porta Cipher but with an extra shift.
Hence we know z=n, e=i, z=n, i=e, y=o, v=r, z=n, y=o, z=n, i=e which gives flag as nineornone
Hence the flag is rtcp{nineornone}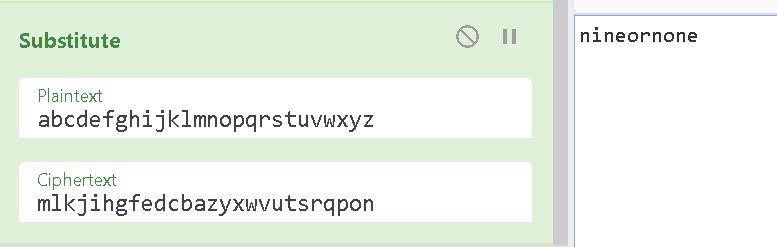
Crypto 1 – CH3COOH
Here a big paragraph is given where the last lines indicate a flag which is given as pmqc{tbbretf_bl_fm_sglv_nlw_qugig_cjxofc}
We can decode this using Vignere Cipher Autokey decode. Decoding it gives us the flag as rtcp{vinegar_on_my_fish_and_chips_please}
Crypto 2 – Fences are cool unless they’re taller than you
The question says jump over fences and gives a string as tat_uiwirc{s_iaaotrc_ahn}pkdb_esg which can indicate this is a railfence cipher
We can decode this by putting the Rails as 3 for railfence and by using rumkin.com/tools
The flag is decoded as tcp{ask_tida_about_rice_washing}r which is nothing but rtcp{ask_tida_about_rice_washing}.
Crypto 3 – Broken Yolks
The question is given as a scramble of letters. Here only creative thinking of mind works and the string given is as follows smdrcboirlreaefd
This can be unscrambled by taking the string given and trying to make words out of the letters which gives words as “scrambled“, “or” and “fried” which is the flag.
The flag is rtcp{scrambled_or_fried}.
Crypto 4 – Post-Homework Death
A text file is given with matrix representations.
We need to multiply matrices to get values
Matrix A ={(1.6 -1.4 1.8); (2.2 -1.8 1.6); (-1 1 -1)}
Matrix B is taken as three values at once in the given array as 37 36 -1 34 27 -7 160 237 56 58 110 44 66 93 22 143 210 49 11 33 22
So if we take first three values it will be
Matrix A (3×3) ={(1.6 -1.4 1.8); (2.2 -1.8 1.6); (-1 1 -1)}
Matrix B (3×1) ={(37) ;(36); (-1)}
Matrix A x Matrix B (3×1)= {(7); (15); (0)}
Now convert this as A=1, B=2, …, Z=26 and 0 as space character. We get “go“.
Similarly take next three values and continue the process as shown above multiplying matrices with Matrix A. We get the flag as rtcp{go_do_your_homework}
Crypto 5 – Parasite
Here this is a little logical and difficult challenge. The text given in the file is morse code which is “ .— -.. ..- — . -.- -.- -.. ..-. .–. ..- ..-. .–. – -.- .— . ..-. .-.. ..- –. . ..- -.- -.-. …. -.- -.- ..- .– ..-. ..- -… . “
Now convert it to text we get JDUMEKKDFPUFPTKJEFLUGEUKCHKKUWFUBE
The hint in the question is SKATS which korean language alphabet.
So we split this string we got into korean based alphabet sounds which form this
JDU MEK KDF PUF PTK JEF LU GEUK CHK KUW FU BE
Now each of these sounds form a letter with combination of SKATS
For example take JDU we will find Hangul representation of the SKATS
J – ㅎ
D – ㅡ
U – ㅣ
Now combining all three SKATS and Hangul representations we get
JDU – 희
Now you can clearly see the alphabet is made up of all three components of SKATS which we discussed.
Hence we got one output similarly do for all the sounds mentioned above which are JDU MEK KDF PUF PTK JEF LU GEUK CHK KUW FU BE
We get the output as 희망은 진정한 기생충입니다
Now translate this from Korean to English we get the words as hope is a true parasite
So the flag is rtcp{hope_is_a_true_parasite}
Forensics 1 – Neko Hero
Download the file given which is an image.

The image contains several layers of data under it which needs to be observed
Open the image for analysis with https://georgeom.net/StegOnline tool.
We can do bit plane analysis on the image and searching for bit planes in the plane of Green 0 we can find a different image

Hence the flag is rtcp{s4vE_@LL_7h3m_c4tG1Rl$}
Forensics 2 – Deep Lyrics
Download the audio file and it contains a secret text file inside it.
To extract the file we need a simple tool which is free to get which is Deep Sound available at http://jpinsoft.net/DeepSound/Download.aspx?Download=LastVersion
Once installed opening the file in the tool gives the following result
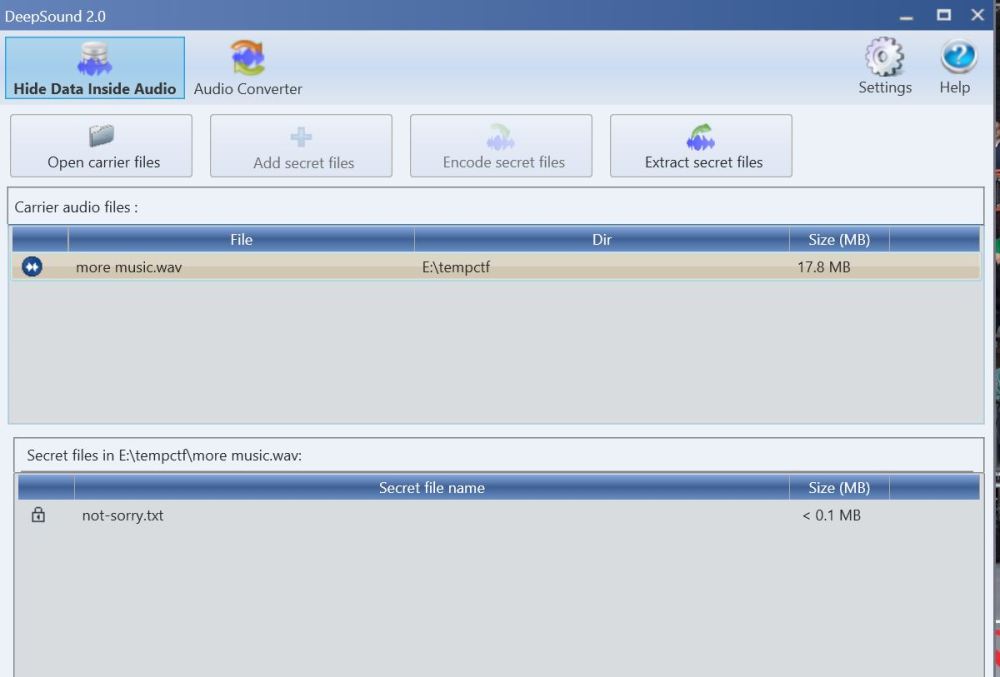
Extract the file out and save it and opening it gives the flag as rtcp{got_youuuuuu}
Misc 1 – Rules
Read rules of the competition to get the flag as rtcp{this_is_not_a_flag_i_think}
Misc 2 – Spilled Milk
Once you download the file you can see there is a flag in all of the white area but it is not visible clearly to eye.
So take the file upload it to https://georgeom.net/StegOnline and then perform a Half – LSB analysis on it to extract the flag or make the flag clearer which gives the following image

The flag is rtcp{Th4nk$_f0r_h3lP1nG!}
Misc 3 – Music Lab
The file given is midi file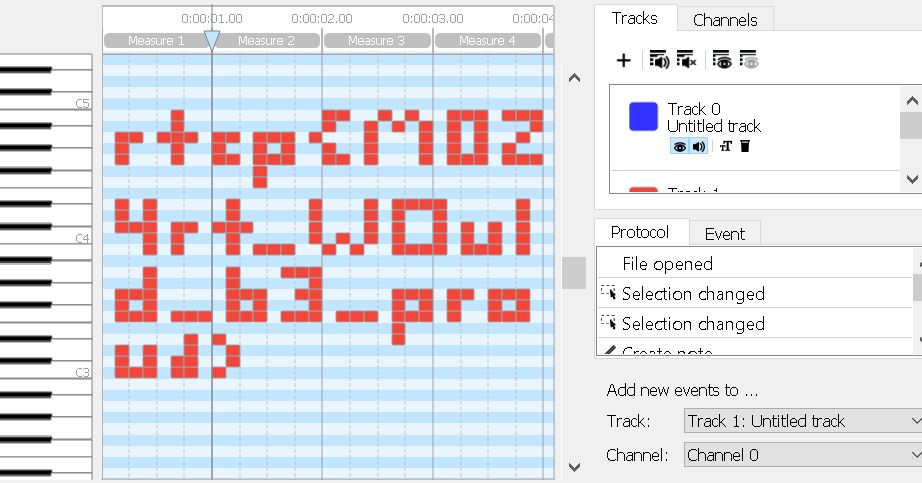
Open the file in any Midi synthesizer to get the flag
Hence from the above picture we get flag as rtcp{M0Z4rt_WOuld_b3_proud}
OSINT 1 – The Drummer who gave all his daughters the same name
What is the value stored in the first registry key created by the virus Anna Kournikova?
The answer to that can be found by reading about the worm which was created which created registry keys as follows
HKEY_USERS\.DEFAULT\Software\OnTheFly
HKEY_USERS\.DEFAULT\Software\OnTheFly\mailed=(1 for yes)
The value stored in the first registry key by the virus is “Worm made with Vbswg 1.50b”
The flag is the same here in this challenge the flag format is not necessary
OSINT 2 – What a sight to see
The google dork used to search for a specific site is asked which is “site:”
For a list of google dorks visit DORKS
Reverse Engineering 1 – EZ
Open the python code file to get two flags which are rtcp{tH1s_i5_4_d3c0Y_fL4g_s0_DoNt_sUbm1T_1t!}
and rtcp{tH1s_i5_4_r3aL_fL4g_s0_Do_sUbm1T_1t!} which is the flag
Reverse Engineering 2 – PZ
Open the python code file and by analysing code
def main():
access = checkpass()
if access == True:
print("Unlocked. The flag is the password.")
print("b-but i wunna show off my catswpeak uwu~... why wont you let me do my nya!!")
exit()
Here we get the main function is accessing checkpass() function to get the flag which contains the actual flag among all dummy functions.
The checkpass function gives the flag as rtcp{iT5_s1mPlY_1n_tH3_C0d3}
Reverse Engineering 3 – LEMON
Download the python code and open it which gives the following
def main():
access = checkpass()
if access == True:
print("Unlocked. The flag is the password.")
print("b-but i wunna show off my catswpeak uwu~... why wont you let me do my nya!!\noh well... good luck with the rest of the ctf :/\nbut I WANT TO SPWEAK CATGIRL NEXT TIME SO YOU BETTER LET ME >:(")
exit()
else:
print("Incorrect password!")
print("sowwy but now you gunnu have to listen to me spweak in cat giwrl")
Again here the main function is accessing the checkpass() function which is given as
def checkpass():
userinput = input("Enter the password: ")
if userinput[0:4] == "rtcp":
if userinput[10:13] == "tHi":
if userinput[22:25] == "cuR":
if userinput[4:7] == "{y3":
if userinput[16:19] == "1nT":
if userinput[7:10] == "4H_":
if userinput[13:16] == "S_a":
if userinput[19:22] == "_sE":
if userinput [25:27] == "3}":
return True
Here we can rearrange the terms in the function according to their location indexes to get the flag
We get first
0: 4 – rtcp
4:7 – {y3
7:10 – 4H_
10:13 – tHi
13:16 – S_a
16:19 – 1nT
19:22 – _sE
22:25 – cuR
25:27 – 3}
Hence the flag is rtcp{y34H_tHiS_a1nT_sEcuR3}
Explore my website, Share, Comment and Like Thank you
